Java is a computer language for getting things done. If you have Java installed on your computer, you have enabled your computer to “talk” this language, which is a good thing.
Problem is, nowadays Java is used primarily to remotely take control of your computer by criminals and use your resources and information to make money. This is a bad thing.
Therefore, I will echo the advice of most computer security experts and suggest that you disable Java for your browsers (Firefox, Internet Explorer, Chrome etc) now.
Windows users are the ones most at risk – there are known exploit kits out there that actively exploit Java to take control of your computer. First, check if you have Java installed on your computer – is there a “Java” icon in Windows’ Control Panel? If not, you have nothing to worry about as you don’t have Java on your computer.
If, as most people, you do have Java installed, don’t worry, it’s easy to secure it: Two steps:
- Update your installation of Java to the latest version released by Oracle here: http://java.com/en/download/manual.jsp – After downloading and installing it, you will have the latest and more secure Java for your computer to use.
- Disable the use of Java in your browsers, by going to Control Panel, then “Java”, and then in the “Security” tab un-ticking the box before “Enable Java content in the browser“.
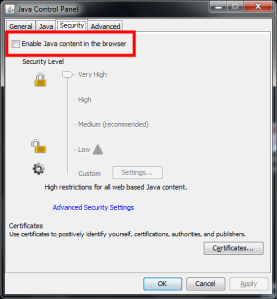
That’s all you need to do.
Note: GNU/Linux and Mac users, you are not out of danger – the same vulnerability can be used to exploit your systems too, so it’s recommended that you disable Java in your browsers as well. See my advice from 2011 about “How much Java do you need?” and Brian Krebs’ recent FAQ for more.